Computers became mandatory to run successful businesses. It’s not enough to possess isolated computer systems. They have to be networked to facilitate communication with external businesses. This exposes them to the surface world and hacking. Hacking means using computers to commit fraudulent acts like fraud, privacy invasion, stealing corporate/personal data. There are some of the types of hackers in this world. Cybercrimes cost many organizations many dollars per annum. Businesses got to protect themselves against such attacks.
Example of Hacking:
Using password cracking algorithm to realize access to a system
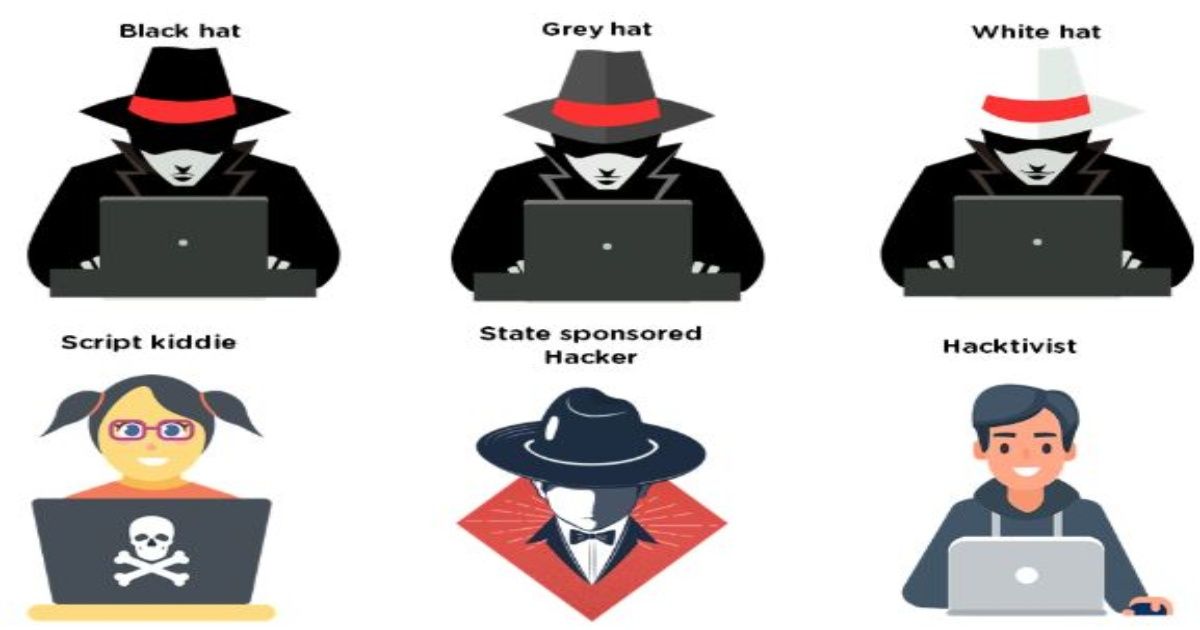
Black Hat Hackers :
There are some of the types of hackers.
The term “black hat” originated from Western movies, where the bad guys wore black hats, and therefore the good guys wore white hats.[1]
A black-hat hacker is a private who attempts to realize unauthorized entry into a system or network to take advantage of them for malicious reasons.
The black-hat hacker doesn’t have any permission or authority to compromise their targets.
They try to inflict damage by compromising security systems, altering functions of internet sites and networks, or shutting down systems.
They often gain access to passwords, financial information, and other personal information. These are one of the types of hackers which affect spirituality.
White Hat Hackers :
White-hat hackers are deemed to be the great guys, working with organizations to strengthen the safety of a system. These are one of the types of hackers which have permission to interact with the targets and to compromise them within the prescribed rules of engagement.
This individual focuses on ethical hacking tools, techniques, and methodologies to secure an organization’s information systems.
Unlike black-hat hackers, ethical hackers exploit security networks and appearance for backdoors once they are legally permitted to try to do so.
White-hat hackers always disclose every vulnerability they find within the company’s security system in order that they are often fixed before they’re being exploited by malicious actors.
Grey Hat – One of the types of Hackers :
There are some of the types of hackers which exploit networks and computer systems similar to black hats. But do so with none malicious intent, disclosing all loopholes and vulnerabilities to enforcement agencies or intelligence agencies.
They can also extort the hacked, offering to correct the defect for a nominal fee.
Blue Hat Hackers :
There are some of the types of hackers aggressive in every way. But as long as you create them. Blue Hat hackers often take existing code for malware and viruses they find online, then modify it to satisfy their needs. They will use this code to focus on the business or individual they feel has wronged them and inflict their revenge.
Generally, only a drag if you’ve made someone very, very angry. This could be a customer, supplier, or employee – anyone who could be so angry that they need to ‘make you pay’.
Red Hat Hackers :
There are some of the types of hackers in the world. These are the caped crusaders of the cyber world. To put a stop to people they know to be Black Hat hackers. But they are downright scary in how they go about it. They essentially take the Black Hat’s arsenal and switch it back against them. Using malware, DoS attacks, viruses, and Trojan Horses to destroy their machines from the inside out. It’s a pretty effective way of stopping them from attacking anyone else.
Red Hat hackers are similar to White Hat ones, in the sense that they are working to put a stop to Black Hat attacks on your business. But you probably won’t know about it.
Green Hat Hackers :
Baby hackers taking their first steps in the cyber world. These are some of the types of hackers. Green Hat hackers are all about the training. They are new to the world of scripting, coding, and hacking in general, so you probably won’t find one attacking. Instead, they lollygag around online message boards asking questions of more developed hackers, honing their skills.
Green Hat hackers don’t really represent a threat to businesses. They are still ‘green’, and more curious about learning the way to hack than actually doing it.
Script Kiddie :
This is something of an ‘odd one out’ since it’s neither a hat or a color! But a Script Kiddie can still cause problems, regardless of how innocent the name sounds.
Script Kiddies have no interest in things as mundane as theft. Or, as it turns out, script. They don’t tend to develop their own software – instead, they download existing malware development software and watch videos on the way to use it. When they’re confident, they’ll attack. A typical Script Kiddie attack would be a DoS (Denial of Service) or DDoS (Distributed Denial of Service). This basically means they flood an IP address with so much useless traffic that it collapses. These are some of the types of hackers. It causes chaos and prevents anyone else from using the service.
While they could not present a financial risk, Script Kiddies are often a pain. They can cause disruption to your business which will damage your reputation or lose your customers, and it can take a while to urge everything back online.
Therefore these are the types of hackers that script out the world.

All you need to know about Data Science
Learn Data Science
| Top 7 Data Science University/ Colleges in India | Top 7 Training Institutes of Data Science |
| Top 7 Online Data Science Training Programs | Top 7 Certification Courses of Data Science |
Learn Data Science with WAC
| Data Science Webinars | Data Science Workshops |
| Data Science Summer Training | Data Science One-on-One Training |
| Data Science Online Summer Training | Data Science Recorded Training |
Other Skills in Demand
| Artificial Intelligence | Data Science |
| Digital Marketing | Business Analytics |
| Big Data | Internet of Things |
| Python Programming | Robotics & Embedded System |
| Android App Development | Machine Learning |